 This documentation is released under the Creative Commons license
This documentation is released under the Creative Commons licenseAttacker wireless ad hoc host. Modificated from WirelessHost module. Redefined from INET framework and used as attacker host.
To implement an attack you must include the corresponding attack controller module in the attacker host.
This attack could be include N attacks controllers to implement several simultaneous attacks. The current attack controllers included are:
See also: AdhocHost, WirelessHost, NA_DroppingAttack, NA_DelayAttack, NA_SinkholeAttack
Author: Gabriel Maciá Fernández, gmacia@ugr.es
Date: 01/22/2013
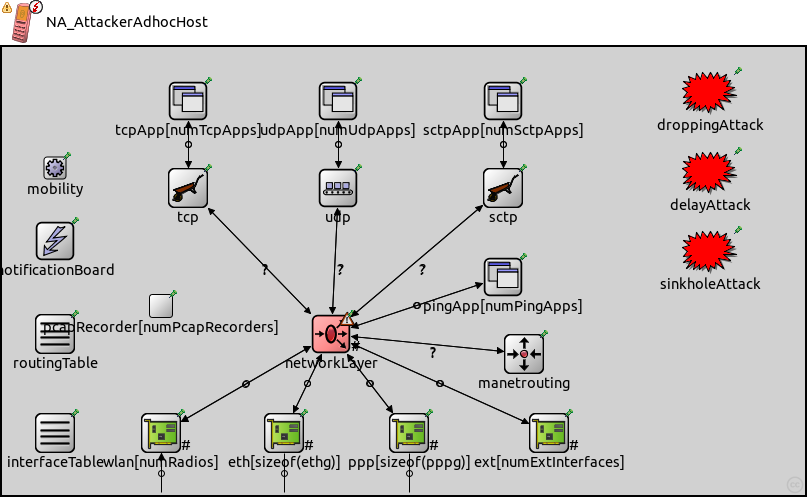
The following diagram shows usage relationships between types. Unresolved types are missing from the diagram.
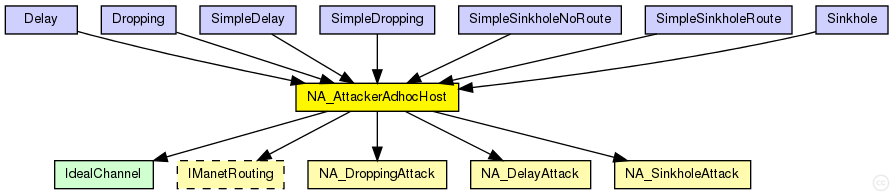
The following diagram shows inheritance relationships for this type. Unresolved types are missing from the diagram.
| Name | Type | Description |
|---|---|---|
| NA_WirelessHost | compound module |
Generic wireless host. Modificated from WirelessHost module. Migrated from INET for inheritance requirements of NA_AttackerAdhocHost and NA_AttackerWirelessHost |
| Name | Type | Description |
|---|---|---|
| Delay | network | (no description) |
| Dropping | network | (no description) |
| SimpleDelay | network | (no description) |
| SimpleDropping | network | (no description) |
| SimpleSinkholeNoRoute | network | (no description) |
| SimpleSinkholeRoute | network | (no description) |
| Sinkhole | network | (no description) |
| Name | Type | Default value | Description |
|---|---|---|---|
| numExtInterfaces | int | 0 | |
| numRadios | int | 1 |
the number of radios in the router. by default no wireless |
| numPcapRecorders | int | 0 |
no of PcapRecorders. |
| mobilityType | string | "StationaryMobility" | |
| routingFile | string | "" | |
| IPForward | bool | true | |
| numTcpApps | int | 0 |
no of TCP apps. Specify the app types in INI file with tcpApp[0..1].typename="TCPEchoApp" syntax |
| numUdpApps | int | 0 |
no of UDP apps. Specify the app types in INI file with udpApp[0..1].typename="UDPVideoStreamCli" syntax |
| numSctpApps | int | 0 |
no of SCTP apps. Specify the app types in INI file with sctpApp[0..1].typename="SCTPServer" syntax |
| numPingApps | int | 0 |
no of PING apps. Specify the app types in INI file with pingApp[0..1].typename="PingApp" syntax |
| tcpType | string | firstAvailable("TCP", "TCP_lwIP", "TCP_NSC", "TCP_None") |
tcp implementation (e.g. ~TCP, ~TCP_lwIP, ~TCP_NSC) or ~TCPSpoof |
| udpType | string | firstAvailable("UDP","UDP_None") | |
| sctpType | string | firstAvailable("SCTP","SCTP_None") | |
| routingProtocol | string | "AODVUU" |
| Name | Value | Description |
|---|---|---|
| display | i=device/cellphone,red;bgb=803,448;i2=status/lightning | |
| node | ||
| labels | node |
| Name | Direction | Size | Description |
|---|---|---|---|
| radioIn [ ] | input | numRadios | |
| pppg [ ] | inout | ||
| ethg [ ] | inout |
| Name | Type | Default value | Description |
|---|---|---|---|
| networkLayer.ip.procDelay | double | 0s | |
| networkLayer.ip.timeToLive | int | 32 | |
| networkLayer.ip.multicastTimeToLive | int | 32 | |
| networkLayer.ip.fragmentTimeout | double | 60s | |
| networkLayer.ip.forceBroadcast | bool | false | |
| networkLayer.arp.retryTimeout | double | 1s |
number seconds ARP waits between retries to resolve an IPv4 address |
| networkLayer.arp.retryCount | int | 3 |
number of times ARP will attempt to resolve an IPv4 address |
| networkLayer.arp.cacheTimeout | double | 120s |
number seconds unused entries in the cache will time out |
| networkLayer.arp.globalARP | bool | false | |
| routingTable.routerId | string | "auto" |
for routers, the router id using IPv4 address dotted notation; specify "auto" to select the highest interface address; should be left empty ("") for hosts |
| routingTable.forwardMulticast | bool | false |
turns multicast forwarding on/off |
| interfaceTable.displayAddresses | bool | true |
whether to display IP addresses on links |
| pcapRecorder.verbose | bool | false |
whether to log packets on the module output |
| pcapRecorder.pcapFile | string | "" |
the PCAP file to be written |
| pcapRecorder.snaplen | int | 65535 |
maximum number of bytes to record per packet |
| pcapRecorder.dumpBadFrames | bool | true |
enable dump of frames with hasBitError |
| pcapRecorder.moduleNamePatterns | string | "wlan[*] eth[*] ppp[*] ext[*]" |
space-separated list of sibling module names to listen on |
| pcapRecorder.sendingSignalNames | string | "packetSentToLower" |
space-separated list of outbound packet signals to subscribe to |
| pcapRecorder.receivingSignalNames | string | "packetReceivedFromLower" |
space-separated list of inbound packet signals to subscribe to |
| droppingAttack.active | bool | false |
Indicates if this attack is active or not in the node |
| droppingAttack.startTime | double | 0s |
Timestamp to start the attack |
| droppingAttack.endTime | double | 0s |
Time instant at which the attack ends, 0 means that the attack will not end during the simulation. |
| droppingAttack.droppingAttackProbability | double | 0 |
Probability of dropping a packet. Range [0,1]. |
| delayAttack.active | bool | false |
Indicates if this attack is active or not in the node |
| delayAttack.startTime | double | 0s |
Timestamp to start the attack |
| delayAttack.endTime | double | 0s |
Time instant at which the attack ends, 0 means that the attack will not end during the simulation. |
| delayAttack.delayAttackProbability | double | 0 |
Probability of delaying a packet. Range [0,1]. |
| delayAttack.delayAttackValue | double | normal(1s, 0.1s) |
Random delay time |
| sinkholeAttack.active | bool | false |
Indicates if this attack is active or not in the node |
| sinkholeAttack.startTime | double | 0s |
Timestamp to start the attack |
| sinkholeAttack.endTime | double | 0s |
Time instant at which the attack ends, 0 means that the attack will not end during the simulation. |
| sinkholeAttack.sinkholeAttackProbability | double | 0 |
Probability of answering a RREQ message with a fake route. Range [0,1]. |
| sinkholeAttack.sinkOnlyWhenRouteInTable | bool | false |
TRUE: Send fake answers to RREQ messages only when requested routes are really in routing table of sinkhole node. FALSE: Send fake answers for any RREQ messages arriving at the sinkhole node. |
| sinkholeAttack.seqnoAdded | double | uniform(20, 30) |
Fake sequence number generated. |
| sinkholeAttack.numHops | int | 1 |
Fake number of hops. |
// // Attacker wireless ad hoc host. Modificated from WirelessHost module. // Redefined from INET framework and used as attacker host. // // To implement an attack you must include the corresponding attack controller module in the attacker host. // // This attack could be include N attacks controllers to implement several simultaneous attacks. // The current attack controllers included are: // - NA_DroppingAttack (dropping attack controller) // - NA_DelayAttack (dropping attack controller) // - NA_SinkholeAttack (dropping attack controller) // // @see AdhocHost, WirelessHost, NA_DroppingAttack, NA_DelayAttack, NA_SinkholeAttack // // @author Gabriel Maciá Fernández, gmacia@ugr.es // @date 01/22/2013 module NA_AttackerAdhocHost extends NA_WirelessHost { parameters: @display("i=device/cellphone,red;bgb=803,448;i2=status/lightning"); wlan[*].mgmtType = default("Ieee80211MgmtAdhoc"); // use adhoc management string routingProtocol @enum("AODVUU","DYMOUM","DYMO","DSRUU","OLSR","OLSR_ETX","DSDV_2","Batman") = default("AODVUU"); IPForward = default(true); submodules: manetrouting: <routingProtocol> like IManetRouting if routingProtocol != "" { @display("p=522,307"); } //# Include dropping attack controller droppingAttack: NA_DroppingAttack { @display("p=708,46"); } //# Include delay attack controller delayAttack: NA_DelayAttack { @display("p=708,126"); } //# Include sinkhole attack controller sinkholeAttack: NA_SinkholeAttack { @display("p=708,205"); } connections: networkLayer.manetOut --> manetrouting.from_ip if routingProtocol != ""; networkLayer.manetIn <-- manetrouting.to_ip if routingProtocol != ""; }